Block Little Snitch Hosts File
So I went slumming on Slashdot (yeah, I know), and came across the ravings of a paranoid Apple user with a blog post titled “Your Computer Isn’t Yours” ( https://sneak.berlin/20201112/your-computer-isnt-yours/ ) laying out all sorts of evil and nasty things happening on you Mac with macOS Big Sur and OCSP and how this is what the great Internet gods Stallman and Doctorow foretold would happen many, many years ago.
Little Snitch 1.2.2 strikes a good balance between automatically blocking potential problems and letting users decide what connections to allow. This is a great tool for anyone who uses a wide. Little Snitch is easy to use and free to try. We also explained how to use Little Snitch 3 to block outgoing connections on a Mac, but here we want to present some better and up-to-date alternatives so that you can choose what is best for you. Unfortunately, until Apple comes up with a solution, OS X users will have to continue using workarounds or dedicated third-party tools for this purpose.
Bullshit.
In spite of my knowing better than to trust this, I let the paranoia in me run wild a bit and went off to Objective Development to download my very own 30-day try-it-out copy of Little Snitch (which is what this is actually all about and why I have their propellor beanie on the page) ( https://www.obdev.at/products/littlesnitch/index.html ). So how did that work out for you, Bill?
I’m glad you asked.
It didn’t work out well at all. After installing version 5.0.2, the anointed version for Big Sur, I would click on it and it would just sit and bounce in the dock for some indeterminate time, then stop bouncing. But nothing showed up anywhere on the desktop, not a window, nothing anywhere. I tried this twice (because I couldn’t believe it the first time). Both times I’d have to kill the instance in the dock. After the second time I just deleted it.
Little Snitch Download
It wouldn’t be so bad if I hadn’t read in the first link about how Apple’s Mac applications just bypass network framework and go directly out to the internet. Which means if it did start up I don’t believe it would do any good if Little Snitch did properly start.
And while poking around Daring Fireball (the site I swore I’d never visit again), I came across a link to another post by a different author titled “Does Apple really log every app you run? A technical look” ( https://blog.jacopo.io/en/post/apple-ocsp/ ). This is a sane and clear explanation of what is actually happening, not the heated rantings coming from “Your Computer Isn’t Yours”. At the very end of the article there’s a three bullet list. The last bullet says “You shouldn’t probably block ocsp.apple.com with Little Snitch or in your hosts file.” Which is what the author of “Your Computer Isn’t Yours” at least implies that’s something you might want to do. I guess it was a good thing Little Snitch refused to start on my MacBook Pro after all.
Little Snitch Iphone
Here is a script to take the hosts from From http://pgl.yoyo.org/adservers/ and convert them to rules for Little Snitch.
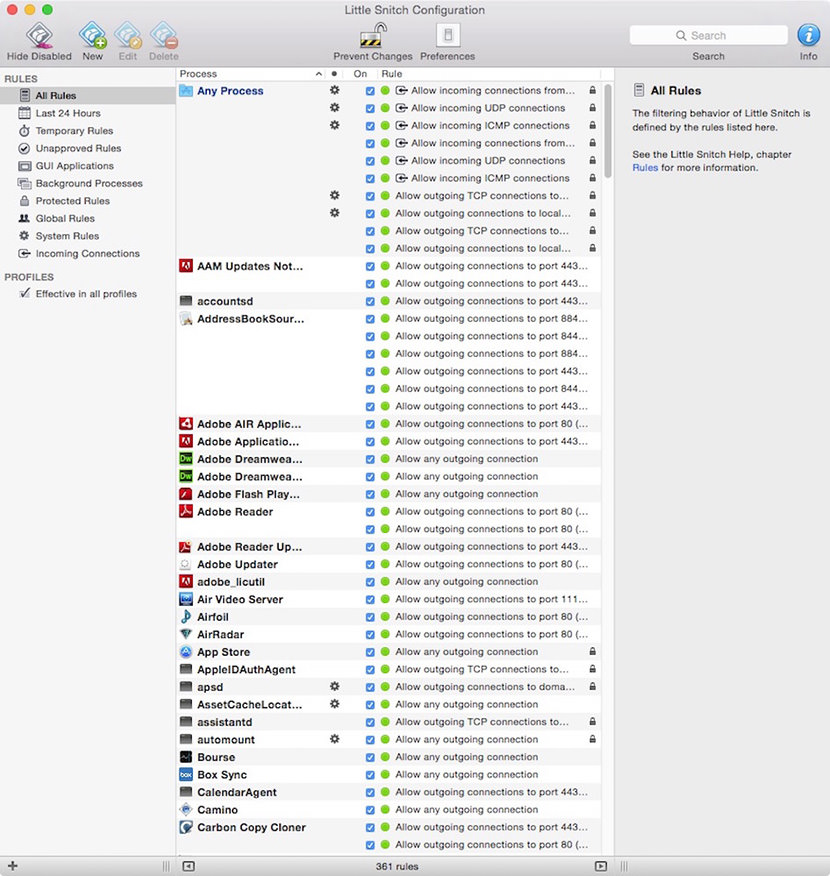
It has options to grab the entire list or grab new entries past a certain date.
Just grab the output and copy/paste into Little Snitch.

The script is written to block access to any process, any port.You can also delete those lines and it will only block Mail.Or use the options to enter any process, port or protocol you want to block.
Installation: Copy the text generated by the output from a plaintext editor into LittleSnitch Rules
Save the script in your home directory, I called mine getadblock.sh.
Make sure to make it executable:
chmod +x getadblock.sh
Output looks like:
File - GetAdblock.sh
Run Command

